Huawei and Joki ICT collaboration on cybersecurity aims to enhance protection against modern threats that are becoming increasingly complex and difficult to manage. New technologies such as big data, cloud computing, and AI create intricate systems that can have vulnerabilities targeted by hackers. The rise in cyberattacks, including ransomware and supply chain hacks, has made it crucial to address these weak spots to ensure safety. Through their partnership, Huawei and Joki ICT leverage their expertise to fortify systems and improve overall security.
Key Takeaways
-
Huawei and Joki ICT work together to improve cybersecurity using smart tools that find and fix problems fast.
-
The Finnish Cybersecurity Act asks companies to handle risks and report issues, making businesses safer and more responsible.
-
Joki ICT’s planned way of managing risks includes finding, checking, and fixing problems to keep their clients safe.
-
Using automation in cybersecurity saves time, lowers mistakes, and helps companies stay ready for new threats.
-
CERT-to-CERT links help share threat details quickly, boosting teamwork and faster responses to cyber risks.
Cybersecurity Challenges and the Finnish Cybersecurity Act
Key Rules of the Finnish Cybersecurity Act
The Finnish Cybersecurity Act sets rules to protect key industries. It asks companies to find and handle risks in their networks and systems. This includes following 12 specific steps to manage risks. These steps focus on technical, operational, and organizational controls, especially fixing weak spots.
Companies must also tell the National Cyber Security Centre Finland (NCSC-FI) about big incidents. This helps respond to threats quickly and keeps cybersecurity open and clear. By requiring these actions, the Act makes critical industries safer.
How the NIS2 Directive Helps Cybersecurity Rules
The NIS2 Directive works with the Finnish Cybersecurity Act to set clear cybersecurity rules. It focuses on managing risks, reporting incidents, and teamwork. The table below shows its main points:
|
Aspect |
Description |
|---|---|
|
Cybersecurity Rules |
Sets clear rules for companies to follow. |
|
Risk Management Steps |
Lists 12 steps companies must take to manage risks. |
|
Incident Reporting |
Requires reporting big incidents to the NCSC-FI. |
|
Teamwork Among Stakeholders |
Encourages teamwork to handle cybersecurity risks better. |
This directive pushes companies to stay ahead in cybersecurity and meet European standards.
Problems with Fixing Weaknesses in Companies
Fixing weaknesses in systems is hard for many companies. Studies show 98% of web apps can be attacked, and 72% of problems come from coding mistakes. Companies also face about 1,636 cyberattacks every week, showing the need for better solutions.
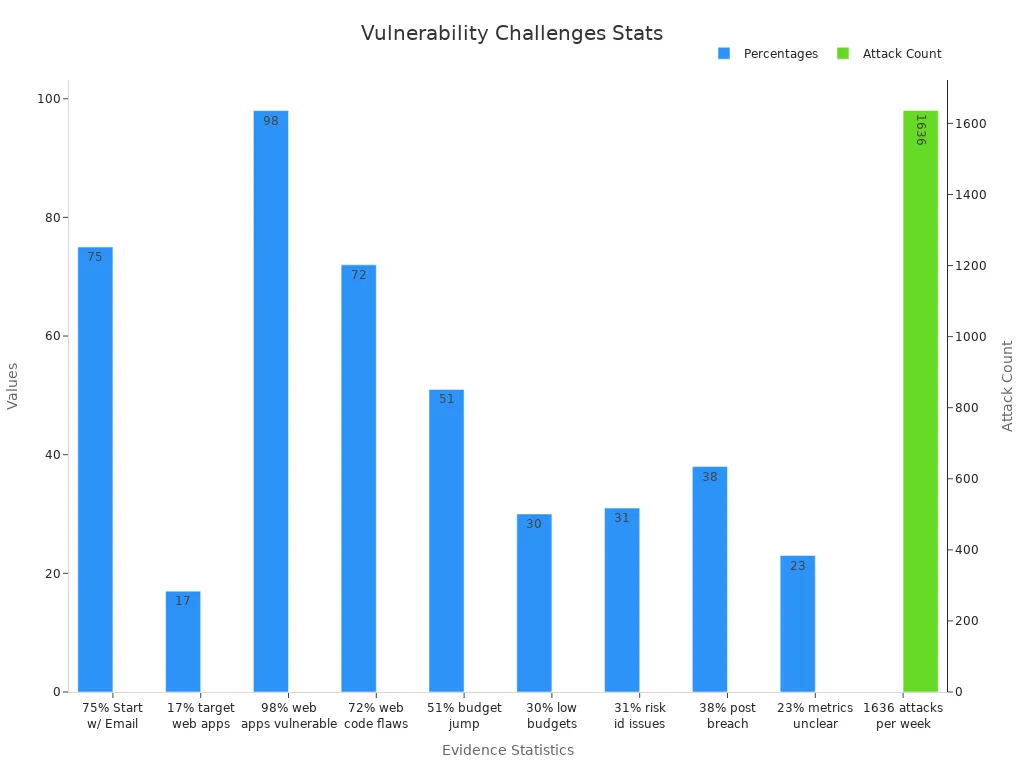
Even with bigger budgets, 30% of leaders think they don’t have enough resources. Only 23% of companies fully understand their cybersecurity numbers. These problems show why using automated tools to fix weaknesses is important for safety and lowering risks.
Joki ICT’s Plan to Handle Security Weaknesses
Goals of Joki ICT’s Security Plan
Joki ICT works to make systems safer by fixing weaknesses early. They check for risks that could harm their systems or their clients’ systems. They also work with others to improve safety for everyone. Joki ICT teaches teams about risks and how to manage them. They find important tasks by spotting weaknesses and fixing them quickly. Watching over these tasks helps keep systems running well and lowers risks.
Steps in Joki ICT’s Weakness Management Plan
Joki ICT uses clear steps to handle system weaknesses. Each step helps find, check, and fix risks. The table below shows the main steps:
|
Step |
What It Does |
|---|---|
|
Finding Weaknesses |
Tools help find weak spots in systems. |
|
Checking and Rating |
Joki ICT checks weak spots and decides which ones are most risky. |
|
Watching and Teamwork |
They watch how fixes are done and keep teams on track. |
|
Testing Fixes |
After fixing, they test to make sure the problem is solved. |
|
Handling Problems |
If a big problem is found, they ask NCSC-FI or Huawei for help. |
|
Sharing Information |
They tell NCSC-FI and clients about problems to help improve national cybersecurity. |
This plan helps Joki ICT fix problems fully, making systems safer.
Tools and Methods, Including Kybermittari
Joki ICT uses smart tools and methods to fix weaknesses. One tool, Kybermittari, checks tasks and ensures they meet ISO27001 rules. This tool helps Joki ICT decide which risks to fix first. They also keep records of changes to help with future risks. By watching for new problems, Joki ICT stays ready for new challenges. These tools and methods help them fix issues fast and keep systems strong.
Huawei’s Role in Automated Vulnerability Management
Automated Solutions for Vulnerability Management
Huawei uses smart tools to find and fix weak spots. These tools make it easier to spot problems and fix them fast. By automating tasks, Huawei reduces mistakes and works better than required rules.
Benefits of Huawei’s automated tools include:
-
Quick sharing of problem details to fix issues faster.
-
Better ways to handle weak spots, going beyond basic rules.
-
Regular updates to keep products safe over time.
These tools help companies stay safe and ready for new cyber risks.
Patch Management and Timely Disclosures
Huawei’s patching system keeps systems strong and safe. They quickly share details about problems and fixes with partners like Joki ICT. This helps companies fix issues fast and avoid risks.
Key parts of Huawei’s patching system are:
-
Regular updates and fixes to keep systems secure.
-
Automated tools that make fixing problems easier and faster.
-
Sharing problem details early so fixes happen quickly.
This focus on quick fixes and updates helps follow safety rules and keeps systems strong.
CERT-to-CERT Interconnections and Collaboration Tools
Huawei helps teams work together using CERT-to-CERT links. These links make sharing important safety details easy. Joki ICT uses Huawei’s tools in its Security Center to find and fix problems better.
Results of this teamwork include:
-
CERTs working together automatically to handle weak spots.
-
Better tracking and fixing of problems in security centers.
-
Easier sharing of problem details using Huawei’s system.
With these tools, Huawei and its partners fix problems faster and keep systems safer.
Huawei’s Principles and Abilities in Handling Vulnerabilities
Focus on Reducing Harm and Acting Early
Huawei works hard to lower risks from weak spots. They share important details about problems quickly with partners. This helps fix issues faster and keeps systems safer. Their goal is to stop risks before they grow.
Teamwork is very important to Huawei. They work with their supply chain to fix problems better. This way of working meets safety rules and helps partners manage risks. Huawei also learns from new threats and improves over time. These actions show their promise to keep systems secure.
PSIRT Team and Bug Bounty Program
Huawei has a special team called PSIRT to handle problems. They run a bug bounty program to find and fix weak spots. This program helps make their systems stronger and safer.
Huawei also has a Security Advisory Portal. This website shares details about problems and how to fix them. They use smart tools to share this information through APIs. These efforts show Huawei’s focus on being open and solving problems well.
|
Feature |
What It Does |
|---|---|
|
Problem Reporting Program |
Managed by PSIRT, includes a bug bounty to find weak spots. |
|
Security Advisory Website |
Shares problem details and solutions for everyone to see. |
|
Smart Problem Sharing |
Uses tools to share problem details quickly and clearly. |
Using Automation with CSAF 2.0 Rules
Huawei uses automation to handle problems faster and better. They follow CSAF 2.0 rules to share details about weak spots. Studies show automation helps companies understand these rules better. About 33% of companies use automation now, and 25% want to start.
Automation helps Huawei fix problems quickly and follow safety rules. By using CSAF 2.0, they show they care about staying safe and solving problems early. This keeps systems strong and ready for new challenges.
Success Story: Huawei and Joki ICT Collaboration on Cybersecurity

Joki ICT’s Role in Municipal Cybersecurity
Joki ICT helps protect city systems from cyber problems. They focus on finding and fixing risks quickly. Their work covers 26 cities, helping with security and handling incidents. Joki ICT uses smart tools to find and stop threats before they grow.
One important step is using CERT-to-CERT connections. This system shares risk details fast and accurately. Joki ICT also uses Huawei’s website to check and report risks. These actions show their dedication to keeping city systems safe.
Achievements Through Collaboration with Huawei
Working with Huawei has brought big improvements in cybersecurity. Together, they use automated tools to work faster and better. Huawei’s Security Advisories help Joki ICT find risks and protect cities more effectively.
Key achievements include:
-
Faster solutions for city clients.
-
CERT-to-CERT system linked with Huawei’s tools.
-
Testing machine-to-machine links for sharing risk details.
-
Easier risk checks using Huawei’s website.
These successes show how Huawei and Joki ICT work together to stop risks early.
Enhanced SOC Operations and Vulnerability Management
The partnership has improved how Joki ICT handles risks. Automated tools help them find and fix problems faster. Huawei’s Security Advisories make it easier to stop cyberattacks.
One result is three new ways to manage risks, including better SOC operations. Machine-to-machine links are being tested to share risk details more easily. These upgrades help cities stay safe and manage risks better.
|
Initiative |
Description |
Measurable Impact |
|---|---|---|
|
CERT-to-CERT interconnection |
Links to Huawei’s tools for sharing risk details |
Faster and better risk management |
|
Vulnerability disclosure website |
Uses Huawei’s site to check and report risks |
Better risk checks and fixes |
|
Security Advisories integration |
Adds Huawei’s tips to SOC operations |
Stronger protection and risk control |
The teamwork between Huawei and Joki ICT shows how partnerships can improve city security and stop cyber risks.
Automation helps solve today’s cybersecurity problems in smart ways. It makes hard tasks easier, saves time, and reacts to threats faster. But for it to work well, companies need a good system to manage their assets. Some groups may not have this system yet. The table below shows how automation helps:
|
Evidence Type |
What It Shows |
|---|---|
|
Feedback from People |
Some think automation can’t fix all problems, like unclear labels. |
|
Data and Numbers |
Automation saves time and uses fewer resources. |
|
Needs for Automation |
A strong asset management system is needed for automation to succeed. |
Huawei and Joki ICT work together to make cities safer with automation. They’ve made big improvements in fixing weak spots and running security centers. By using smart tools and acting early, they show how to protect important systems from new dangers.
What is the Finnish Cybersecurity Act, and why does it matter?
The Finnish Cybersecurity Act sets rules to protect key industries. It asks companies to find risks, fix problems, and report big issues to NCSC-FI. This helps them stay ready and open about handling cyber threats.
How does automation help manage vulnerabilities?
Automation makes fixing weak spots faster and easier. It finds risks, ranks them, and fixes them quickly. It also lowers mistakes, keeps systems updated, and follows safety rules. Automated tools save time and help handle threats better.
What does Joki ICT do for city cybersecurity?
Joki ICT helps keep city systems safe from cyber problems. They check for risks, fix them, and watch over systems. They protect 26 cities using smart tools like Kybermittari and work with Huawei. Their quick actions make cities safer.
How does Huawei share vulnerability details quickly?
Huawei uses smart tools to share problem details fast. Their patch system gives regular updates and works with partners like Joki ICT. By following rules like CSAF 2.0, they fix problems quickly and stay clear about safety.
What are CERT-to-CERT links, and why are they useful?
CERT-to-CERT links let teams share threat details easily. These links help teams work together, fix problems faster, and improve safety. Huawei and Joki ICT use this system to keep city systems secure.
See Also
RV1126 Enhances Robotics Through AI Edge Computing Solutions
The Role of Innovative Technology in Electronics Excellence
Three Key Innovations of XCF01SVOG20C in Automation
Integrating AEAT-8800-Q24 to Boost Robotics Efficiency
Three Transformative Impacts of ATIC83E2 on Automation